


-
它是拉樣式的
-
它方便使用文字方式來配置,有利於配置版本化
-
外掛太多了,想要監控什麼,基本都會有現成的
-
以上三者,我基本都要重新學,我為什麼不學一個 Google SRE 書上推薦的呢?

-
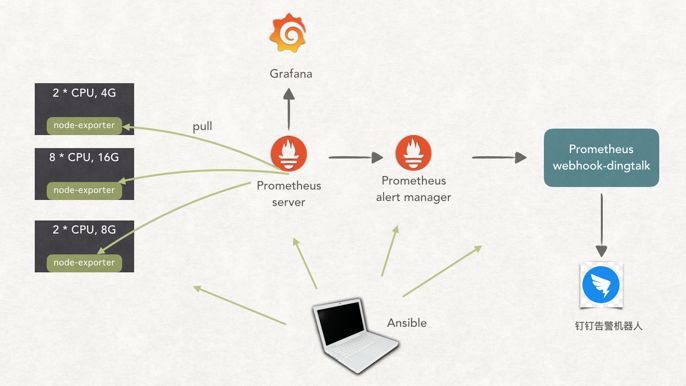
Prometheus Server 負責監控資料收集和儲存
-
Prometheus Alert manager 負責根據告警規則進行告警,可整合很多告警通道
-
node-exporter[1] 的作用就是從機器讀取指標,然後暴露一個 http 服務,Prometheus 就是從這個服務中收集監控指標。當然 Prometheus 官方還有各種各樣的 exporter。



├── environments/ # Parent directory for our environment-specific directories
│ │
│ ├── dev/ # Contains all files specific to the dev environment
│ │ ├── group_vars/ # dev specific group_vars files
│ │ │ ├── all
│ │ │ ├── db
│ │ │ └── web
│ │ └── hosts # Contains only the hosts in the dev environment
│ │
│ ├── prod/ # Contains all files specific to the prod environment
│ │ ├── group_vars/ # prod specific group_vars files
│ │ │ ├── all
│ │ │ ├── db
│ │ │ └── web
│ │ └── hosts # Contains only the hosts in the prod environment
│ │
│ └── stage/ # Contains all files specific to the stage environment
│ ├── group_vars/ # stage specific group_vars files
│ │ ├── all
│ │ ├── db
│ │ └── web
│ └── hosts # Contains only the hosts in the stage environment
│

---
- hosts: all
vars:
jenkins_plugins:
- blueocean
- ghprb
- greenballs
- workflow-aggregator
jenkins_plugin_timeout: 120
pre_tasks:
- include_tasks: java-8.yml
roles:
- geerlingguy.java
- ansible-role-jenkins
-
介面上設定
-
使用 Jenkinsfile:類似於 Dockerfile 的一種文字檔案,具體介紹:Using a Jenkinsfile[7]
pipeline {
agent any
stages {
stage('Build') {
steps {
sh './gradlew clean build'
archiveArtifacts artifacts: '**/target/*.jar', fingerprint: true
}
}
}
}


-
在 Jenkins 安裝 Ansible 外掛[8]
-
在 Jenkinsfile 中執行
withCredentials([sshUserPrivateKey(keyFileVariable:"deploy_private",credentialsId:"deploy"),file(credentialsId: 'vault_password', variable: 'vault_password')]) {
ansiblePlaybook vaultCredentialsId: 'vault_password', inventory: "environments/prod", playbook: "playbook.yaml",
extraVars:[
ansible_ssh_private_key_file: [value: "${deploy_private}", hidden: true],
build_number: [value: "${params.build_number}", hidden: false]
]
}
-
ansiblePlaybook 是 Jenkins ansible 外掛提供的 pipeline 語法,類似手工執行:ansible-playbook 。
-
withCredentials 是 Credentials Binding[9] 外掛的語法,用於取用一些敏感資訊,比如執行 Ansible 時需要的 ssh key 及 Ansible Vault 密碼。
-
一些敏感配置變數,我們使用 Ansible Vault[10] 技術加密。




-
上基礎監控
-
上 Gitlab
-
上 Jenkins,並整合 Gitlab
-
使用 Jenkins 實現自動編譯打包
-
使用 Jenkins 執行 Ansible
-
CMDB的建設:我們使用 ansible-cmdb[12] 根據 inventory 自動生成當前所有機器的情況
-
釋出管理:Jenkins 上可以對釋出的每個階段進行定製。藍綠釋出等釋出方式可以使用透過修改 Ansible 指令碼和 Inventory 實現。
-
自動擴縮容:透過配置 Prometheus 告警規則,呼叫相應 webhook 就可以實現
-
ChatOps:ChatOps實戰[13]
-
https://github.com/prometheus/node_exporter
-
https://github.com/ernestas-poskus/ansible-prometheus
-
https://github.com/timonwong/prometheus-webhook-dingtalk
-
https://www.digitalocean.com/community/tutorials/how-to-manage-multistage-environments-with-ansible
-
http://docs.ansible.com/ansible/latest/modules/consul_module.html
-
https://github.com/geerlingguy/ansible-role-jenkins
-
https://jenkins.io/doc/book/pipeline/jenkinsfile/
-
https://wiki.jenkins.io/display/JENKINS/Ansible+Plugin
-
https://jenkins.io/doc/pipeline/steps/credentials-binding/
-
http://docs.ansible.com/ansible/2.5/user_guide/vault.html
-
https://github.com/audreyr/cookiecutter
-
https://github.com/fboender/ansible-cmdb
-
https://showme.codes/2017-10-08/chatops-in-action/


 知識星球
知識星球